User Roles and Entitlements
Roles
User roles can be customized to grant specific entitlements with various degrees of access. Users can be granted more than one role, but once roles have been assigned, the user will only have access to the entitlements specified in the role's details.
To create a new role:
- On the Users page, click Roles.
- On the first panel, click Add.
- On the Add Role dialog, enter the role name and click Add.
- Enable entitlements and click Save.
To rename a role:
- On the Users page, click Roles.
- Select the role and click Rename.
- On the Rename Role dialog, enter and new name and click Rename.
NOTE: The Administrator role cannot be renamed.
To delete a role:
- On the Users page, click Roles.
- Select the role and click Delete.
- On the Delete role dialog, click Delete.
To modify a role:
- On the Users page, click Roles.
- Select the role.
- Make the changes and click Save.
Entitlements
Users are assigned roles with varying
degrees of entitlements. These entitlements allow users access to
certain features, functions, and actions. Once roles are assigned,
users will only have access to the entitlements determined by their
assigned role(s).
The only exception, before assigning roles,
is the Administrator role. By default, Administrators have access
to all entitlements.
Entitlements can be set for applications, devices, users, reservations, system, and system notices.
WARNING: Some entitlements depend on others to work as intended. e.g., the create reservation entitlement requires the user to also have access to the device list entitlement in order to connect to devices and create a reservation.
Application entitlements:
| Entitlement | Definition | Tester |
|---|---|---|
| Application area access | Permits access to the Applications area. By itself, this is not a security measure. |  |
| Application list | Permits viewing the list of stored applications. |  |
| Application upload | Permits uploading of applications for availability to users with ApplicationList. | |
| Application download | Permits downloading of any stored application to user’s local system. | |
| Application modify | Permits renaming of store applications | |
| Application delete | Permits permanent deletion of any stored application. |
Device entitlements:
| Entitlement | Definition | Tester |
|---|---|---|
| Device area access | Permits access to the Devices area. By itself, this is not a security measure. |  |
| Device list | Permits viewing of connected devices and their states. |  |
| Device modify | Permits renaming of the device, changing the note and assigned slot number. | |
| Device enablement | Permits enabling and disabling devices. Enabled devices count toward the license limit. | |
| Device delete | Permits permanently deleting any disconnected device. | |
| Device connect | Permits connecting to a device. |  |
| Device application management | Permits installing and uninstalling of applications on a device. |  |
| Device release any | Permits releasing of any retained device. Without, user may still release a device they have retained. | |
| Device reboot | Permits rebooting of devices. |
User entitlements:
| Entitlement | Definition | Tester |
|---|---|---|
| User area access | Permits access to the Users area. By itself, this is not a security measure. |  |
| User list | Permits viewing names of all users in the system. |  |
| User modify | Permits editing of a users details. Does permit changing of user names and activating/deactivating/deleting accounts. Does not permit changing of user roles. | |
| User modify role | Permits editing which roles are assigned to any user. | |
| User modify self | Permits a user to modify their own user details. Does not permit changing of user name, user roles, or activating/deactivating account. |  |
| User create | Permits creation of new users. | |
| User export | Permits the user table to be exported. | |
| User import | Permits a user table to be imported. | |
| User roles modify | Permits the modification, deletion, and creation of user roles. |
Reservation entitlements:
| Entitlement | Definition | Tester |
|---|---|---|
| Reservation area access | Permits access to the Reservations area. By itself, this is not a security measure. |  |
| Reservation list | Permits viewing of reservations made by any user. Without, a user can only see reservations created by themselves. |  |
| Reservation create | Permits creation of new reservations. |  |
| Reservation delete any | Permits deletion of any reservation. Without, a user can still delete reservations created by themselves. |
System entitlements:
| Entitlement | Definition | Tester |
|---|---|---|
| System configuration area access | Permits access to the System area. By itself, this is not a security measure. | |
| Export logs | Permits user to export system logs. | |
| Service restart | Permits user to restart services. While services are restarting, GigaFox can not be used. | |
| Empty trash | Permits user to remove unused service files. | |
| Manage iOS system application | Permits user to upload new iOS deviceControl applications and view the state of provisioning profiles and signing keys available on the GEM. | |
| Manage system settings | Permits user to alter administrative system settings for deviceControl. | |
| View Gateways | Permits user to view the status of connected device gateways and the associated USB hubs/ports. | |
| Manage USB hubs | Permits user to change the state of USB hub ports connected to device gateways, and perform other administrative actions such as reboot. | |
| Manage GigaFox license | Permits user to replace GigaFox’s license with any new valid license file. |
System Notices entitlements:
| Entitlement | Definition | Tester |
|---|---|---|
| GigaFox license expiration | Permits user to see the global notice about pending GigaFox license expiration. |  |
| iOS provisioning issues | Permits user to see global notices regarding iOS provisioning issues. |  |
Device Access Controls
By enabling the Device Access Controls feature, GigaFox allows users to be given explicit device access by assigning devices to individual roles. Once Device Access Controls is enabled and devices are assigned to each role, the user’s device list will only display the devices their role(s) allow access to.
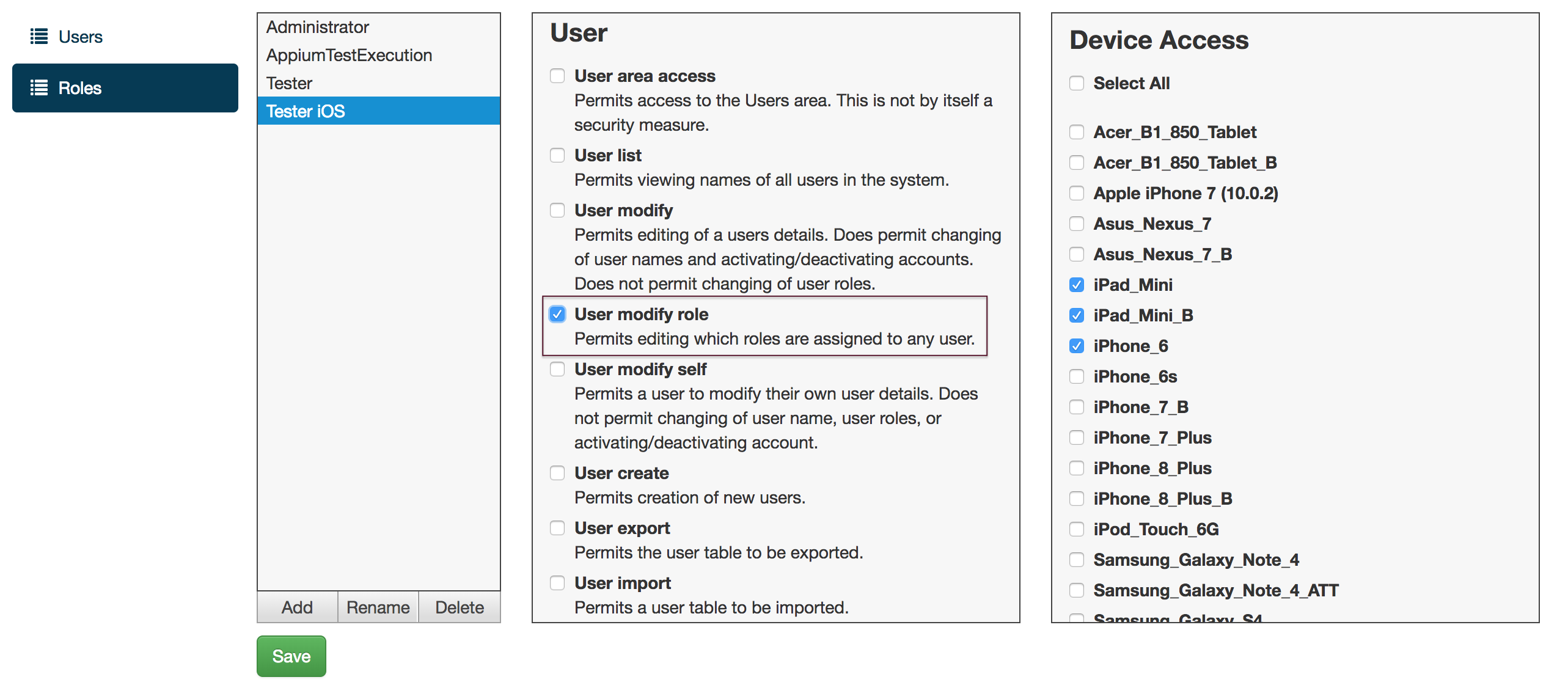
NOTE: Only the Administrator or users with the User roles modify role are granted access to Device Access Controls, the Device Access panel, and its settings. While enabled, only these roles will have access to all available devices at all times.
To enable Device Access Controls and assign devices:
- On the System tab, scroll down to Device Access Controls and enable the Enforce Device Access Controls checkbox.
- On the Users tab, click Roles.
- Select a role.
- On the Device Access panel, select the device(s) to assign to that role and click Save.
To disable Device Access Controls:
- On the System tab, scroll down to Device Access Controls and disable the Enforce Device Access Controls checkbox.
Device Access Controls Entitlement
To grant a non-administrator user access to the Device Access Controls entitlement:
- On the Users tab, click Roles.
- Select a role.
- On the entitlement panel, select User roles modify entitlement and Click Save.